FACES2
Project Methodology
FACES2
At Visiontech Consulting, our project methodology for implementing a custom access control system is designed to ensure
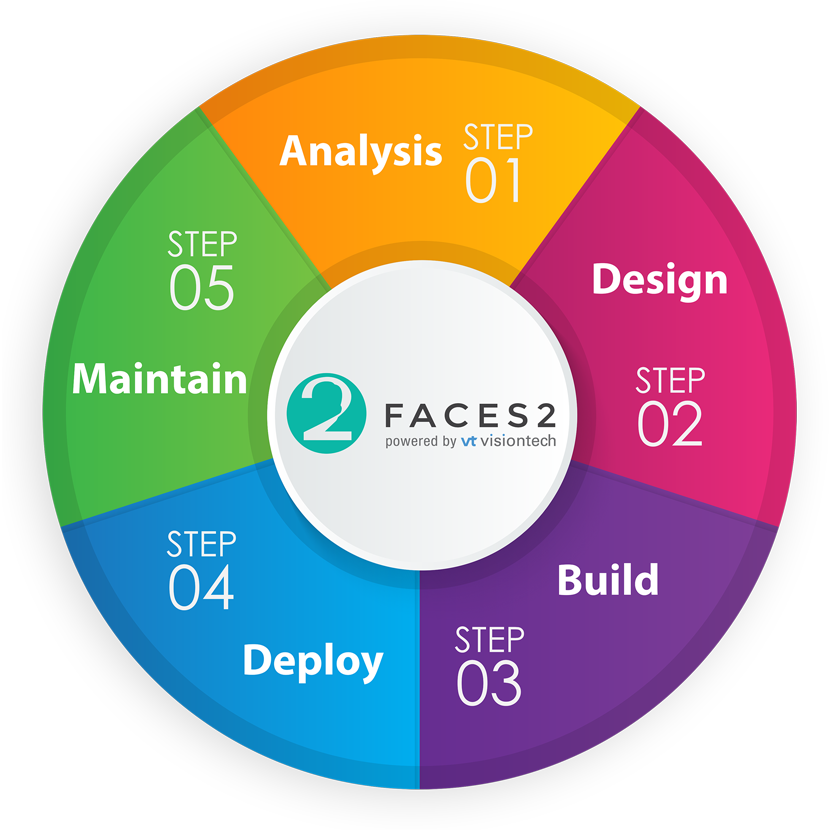
thorough planning, efficient execution, and continuous improvement. Our approach is structured into distinct phases:
Analysis, Design, Build, Deploy, and Maintain. Each phase is carefully crafted to deliver specific deliverables,
achieve key milestones, and complete essential tasks that collectively drive the project towards successful completion.
Our methodology emphasizes thorough planning, stakeholder involvement, and continuous improvement, ensuring that each project
phase is completed successfully and the final system meets all requirements and expectations.
Project Phases
1. Analysis
- The Analysis phase focuses on understanding the project requirements, assessing feasibility, and defining the project scope. Through comprehensive stakeholder engagement, feasibility studies, and detailed system analysis, we gather and validate all necessary information to lay a solid foundation for the project.
2. Design
- In the Design phase, we transform the gathered requirements into detailed design specifications. This phase involves defining the system architecture, developing detailed design documents, creating prototypes, and ensuring compliance with security and regulatory standards. The objective is to provide a clear and actionable blueprint for the development team.
3. Build
- The Build phase is where the system components are developed, integrated, and tested. We set up development environments, write and integrate code, and conduct rigorous testing to ensure that each component functions correctly and that the entire system performs as intended. Comprehensive documentation and quality assurance are key aspects of this phase.
4. Deploy
- During the Deploy phase, we meticulously plan and execute the system's deployment. This involves preparing the production environment, migrating data, installing and configuring the system, and conducting initial testing. User training and support are provided to ensure a smooth transition. The system is then launched and closely monitored for any issues.
5. Maintain
- The Maintain phase ensures the system's ongoing functionality and performance. We provide continuous support, apply regular updates, monitor performance, and implement optimizations. Regular security audits, user feedback, and lifecycle planning ensure that the system remains secure, efficient, and aligned with evolving needs.
Book a consultation now with one of our business development specialists to discover how FACES2 can improve your access control security.



